Articles
Managing router query parameters in Vue.js

URL query parameters are a convenient way to store the state of a view so that the user can return to it using the back button after navigating away. This short article introduces a method to add parameters to the current URL.
IoT RFID reader
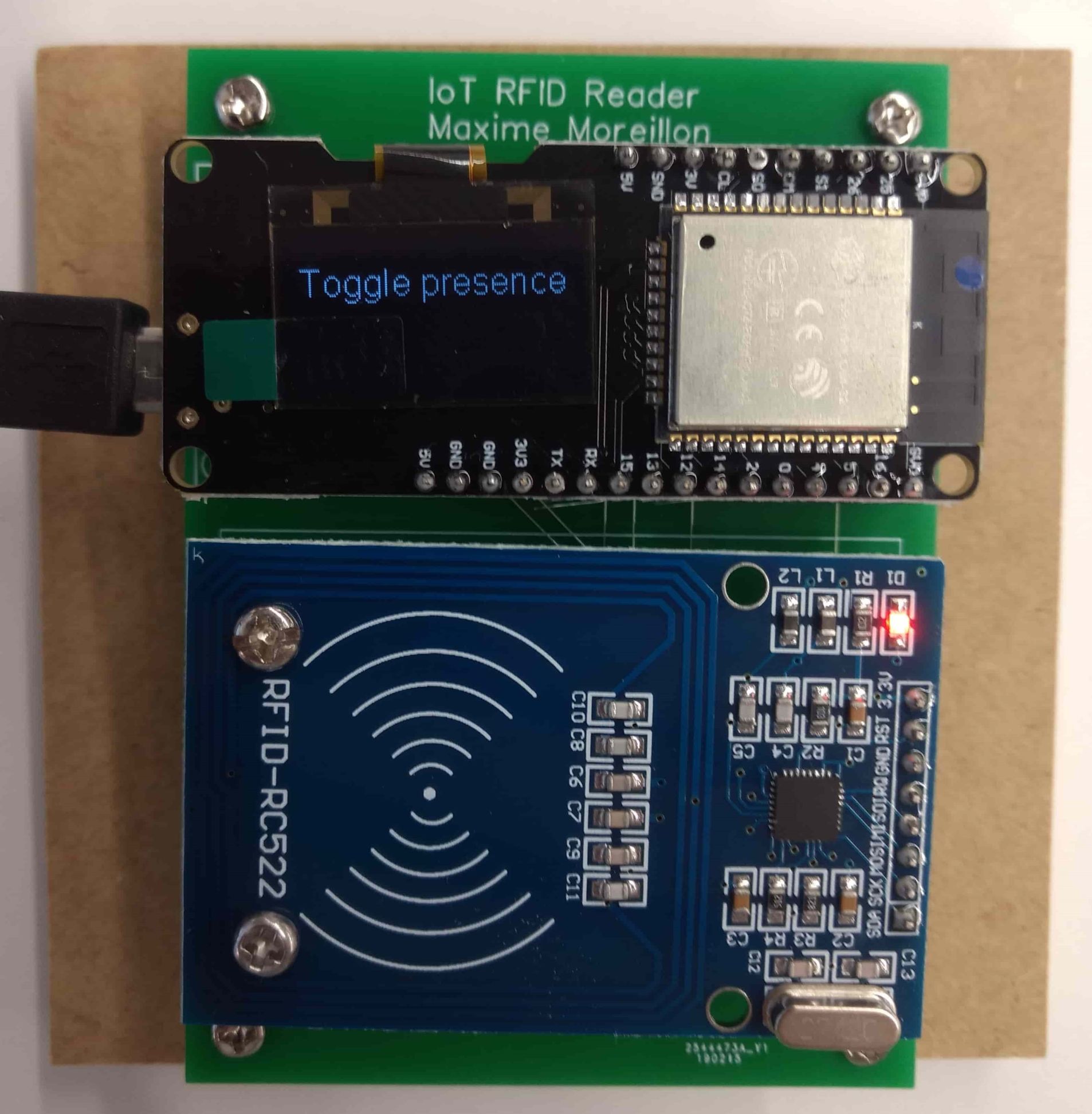
RFID is a conveninent technology for access control and authentication. In this project, I connected an RC522 RFID reader to an ESP32 in order to use it for IoT applications. Additionally, to provide feedback to the user, the ESP32 is also connected to an SSD1306 OLED display and a buzzer. I chose an ESP32 over an ESP8266 simply because of the amount of GPIOs required.
Encrypted Mosquitto broker in Kubernetes

Mosquitto can usually be installed on an Ubuntu server fairly easily using the APT package manager. By Default, the broker handles unencrypted MQTT connections but it can be configured to use SSL certificates obtained, for example, using Certbot and thus enable MQTTs connections. This configuration is usually achieved by editing the Mosquitto configuration file in /etc/mosquitto so as to point to certificates obtained independently. However, when deploying Mosquitto to Kubernetes, one would prefer not to edit configuration files manually after install. Moreover, in Kubernetes, one can use Cert-manager to obtain SSL certificates. Thus, this article presents an efficient method to deploy a secure MQTTs broker in Kubernetes.
"Resizing" a PVC and its PV in Microk8s
With the storage addon enabled, microk8s can automatically provision a PV when a PVC is created. The size of the PV is set according to that of the PVC. However, PVCs cannot be resized after creation. The PVC could be deleted and recreated with a larger size but this would result in the deletion of the PV and, by extension, all the data stored so far in it. This article presents a workaround to resize a PVC and its corresponding PV without any loss of data.
Cashless payment system

A company I worked for had a coffee machine for which employees could purchase coffee. However, the payment was done by putting coins in a jar. Not only did this present the obvious risk of theft, this system was also impractical for people not carrying spare change at all time. I decided to solve this issue by designing this cashless payment system.
Getting Python's requests library to use a local DNS (Core-DNS, Docker-compose, etc.) while behind a proxy
When using Python's requests library, the requests are send through the proxy set as environment variables. Consequently, if the DNS to be used comes before said proxy, the host might not be resolved. This typically happens when resolving a host in Kubernetes using Core-DNS. If the request first leaves the Kubernetes cluster to reach the proxy, then the DNS server becomes unreachable, making the request fail.
IoT EM4305 RFID Reader

RFID tags come in various forms and sizes, from standard plastic cards to chips that can be implanted in one's hand. I got particularly interested in RFID rings, which can be purchased online for less than USD 20$. Those are based on EM4305 chips, which require a compatible reader. Thus, I designed an IoT EM4305 reader that can exchange data over MQTT with other devices.
HUD Goggles

This headset enables the overlay of information on top of its user's field of view. The field of view of the user is captured by a camera and then fed to video goggles, while a MAX7456 OSD chip overlays text on the video feed.
Solving Kong latency problems in Kubernetes

Kong is a popular API gateway that can be used as a reverse proxy for clients to access back-end services. It can be run as a Docker container and, as such, can be deployed to Kubernetes. However, when doing so, requests might be severely impacted by unusually high latency. This can be solved by configuring the order in which Kong resolves DNS records.
IoT lock
Have you ever left your apartment and couldn't remember if you locked your front door or not? Sadly, if it is unlocked, there is not much you can do about it until you get back home. This system is an attempt to solve the problem. Simply put, it consists of attaching an actuator to the door's original locking mechanism control it with through WiFi.